Every day, most of us transmit personal data over the Internet. Secure communication is thus an absolute necessity. In a new article in Nature Photonics, researchers from DTU Physics show that quantum-encrypted signals can be sent via open transmission masts and still be 100 per cent secure, even if hackers listen in.
As we are sending more and more personal data over the Internet, the extent of identity theft is increasing. And in future, the problem will only get bigger. With the development of the ultra-fast quantum computers, all codes could be decrypted in just a few moments. Physicists all over the world are therefore working hard to develop an encoding system which can never be broken.
Challenges of quantum cryptography
Such secure systems are called quantum encryption and are based on the most fundamental laws of physics—quantum physics. According to this branch of physics, codes can be created in such a way that they cannot be intercepted by a third party without the reading destroying the code—thus revealing that a hacker is listening in.
However, quantum cryptography will have to solve two major challenges before our Internet activities are safe and secure: Sending and decoding encrypted quantum signals requires highly specialised equipment, and it is not yet possible to send quantum signals across distances longer than a major European city like Copenhagen.
Secure communication now possible through public channels
In collaboration with researchers from the University of York, Canadian University of Toronto, and MIT, researchers from DTU Physics have now proved that quantum-encrypted signals can be sent via open, i.e. unsecured transmission masts and still be secure, even if a hacker controls the mast. Even though the hacker gets access to all the measurements made by the mast, it will not help him or her snatch the secret key needed to decode the encrypted signals.
Alice and Bob take Eve out
The principle is that when two people are to exchange information, both the quantum-encrypted message and the key, which will subsequently be used to decode the secret message, will exchanged as light signals. In quantum physics, the two persons are typically called Alice (A) and Bob (B).
Alice and Bob send their respective laser light to the transmission mast. Before sending the light, they assign random intensities to their light beams. These are the light intensities that the mast measures; α is the value of the light which Alice sends and β is the value sent by Bob. The mast measures the light intensities and the result γ (α + β) is broadcast publicly for everyone to listen in. It is not secret. When Alice receives γ, she can quite easily find out what β is because α + β = γ, and Alice knows α and γ. The same applies to Bob when he has to find α and knows β and γ.
In this way, Alice and Bob can share a series of numbers known only to them. Eve, which is the quantum physicists’ nickname for the unwelcome spy, cannot use the number for anything, because she does not know α or β, so you could—in principle—have Eve control the relay and she would still would not be able to do anything with the information.
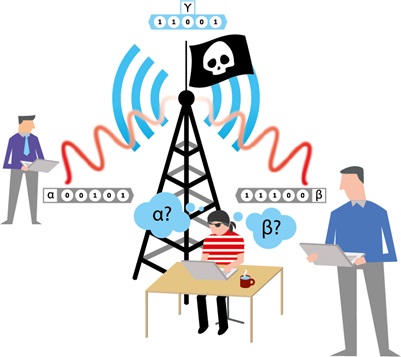
The principle of exchanging quantum-encrypted information via open transmission masts: Alice and Bob send their light beam (red waves, α and β) with random intensity to the transmission mast. The transmission mast measures the light intensities and broadcasts the result (γ). The hacker Eve can snatch the γ-signal, but is unable to tell which parts of the signal correspond to α and β.
An obvious objection would now be that if Eve controls the relay, she can determine which γ-value she wants to announce. However, Eve will gain nothing from lying about γ, because Alice and Bob can compare parts of their secret key. If Eve lies about γ, Alice and Bob will discover that they do not have the same key, which will set off the alarm.
Less need for advanced technology
Thus, the exchange of quantum information takes place by means of a completely open transmitting mast. This reduces the previous requirements for secure networks and advanced measuring equipment for the distribution of the secret keys that used to decode the encrypted information. This is a major step toward the secure Internet traffic of the future.
Read the article in Nature Photonics
Quantum cryptography